For more than 15 years, there have been various predictions from tech leaders about the death of passwords. Bill Gates predicted it back in 2004 and Microsoft has predicted it for 2021. There have been numerous similar proclamations in between, alongside ongoing criticism of passwords as an inadequate means of protection.
Yet passwords remain a common aspect of cybersecurity, something people use every day. What’s more, passwords show little sign of disappearing yet. But many people still use them badly and seem unaware of recommended good practice.
World Password Day on May 6 is a good time to reflect on our use of passwords and how to promote better password habits.
It’s very common for cybersecurity experts and companies to blame users for using passwords poorly, without recognising that systems permit their poor choices.
Many websites offer no upfront guidance on how to choose the passwords they require us to have, perhaps assuming we know these things already or can find it out elsewhere. But the fact that people persist in using weak passwords suggests this is an optimistic view.
Outdated advice
In addition to lacking guidance, it’s common to find websites enforcing outdated password requirements. You’re probably familiar with systems insisting on password complexity, by requiring upper case letters, numbers or special characters to make passwords stronger (our response to which often mirrors the video below).
However, the current guidance is to allow complexity but not to require it, and to basically regard password strength as synonymous with password length.
The National Cyber Security Centre recommends creating a long password by combining three random words, enabling something longer and more memorable than many standard choices.
My password attempts
Also unhelpful is that, rather than giving guidance and requirements at the outset, many sites only reveal rules in response to us trying things that aren’t allowed. I tried creating a password for one such site. Most of my attempts received feedback requiring further action, until I settled on a final choice, which was accepted without complaint. But the password that was accepted, steve!, was short and rather predictable.
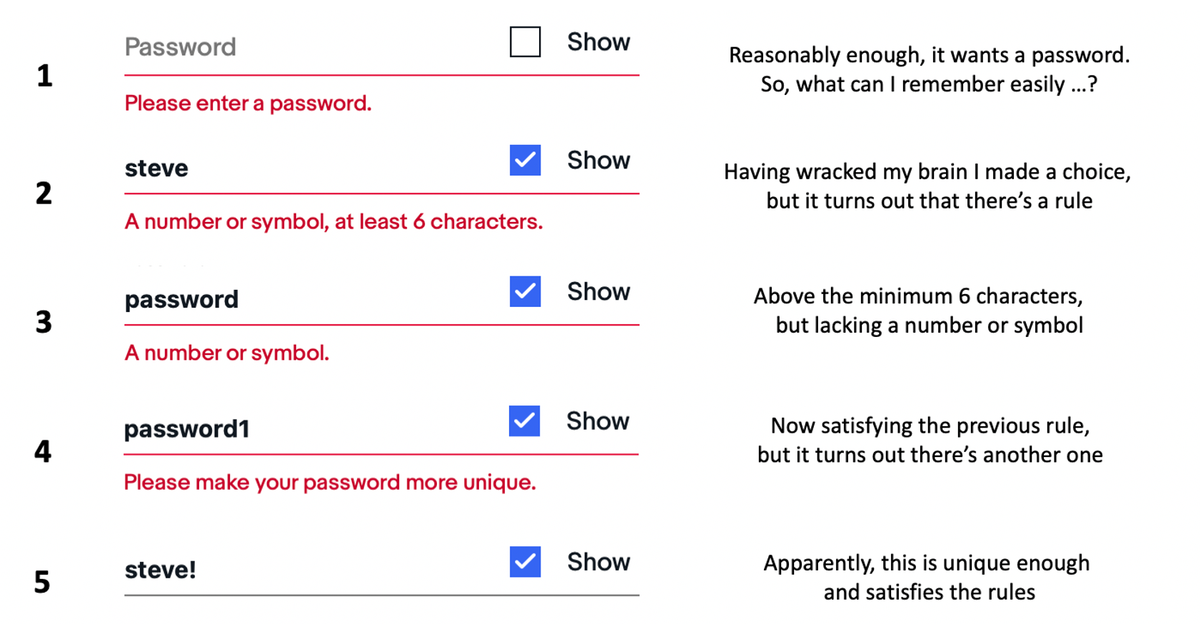
When I played around a bit more, various other weak choices were accepted. For example 1234a!, abcde1 and qwert! all satisfied the rules, as did Furnell1 – which isn’t particularly strong, especially as I already entered Furnell as my last name elsewhere on the sign-up form.
Meanwhile, the rules often mean we can’t use passwords our devices auto-generate for us, or ones we might create for ourselves by following current guidance.
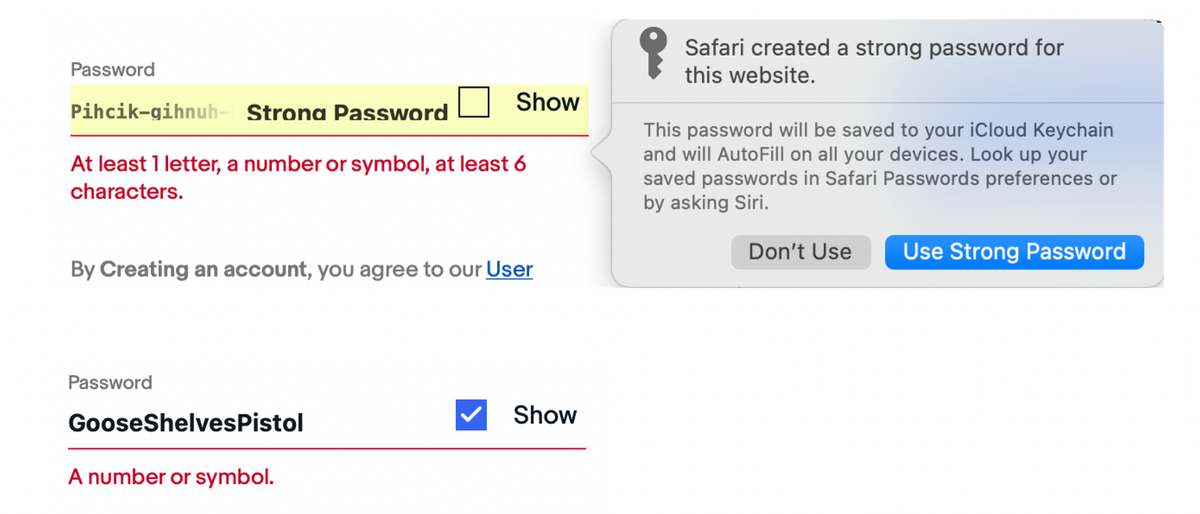
Some sites seem to think they can compensate for a lack of guidance by using techniques such as password meters to rate our choices. However, while these give feedback, they’re not a substitute for providing guidance on what good looks like.
Using another site, I entered a poor password (the word password), and the only feedback I received was that the password is very weak. If a user was genuinely offering this password as an attempt, what they need to be told is why it’s weak. While you can doubtless find some sites giving better and more informative feedback, this example is unfortunately representative of many others.
Rules to follow
Of course, having highlighted the lack of effective guidance, it would be remiss to end without actually offering some. The NCSC’s guidance about choosing and using passwords are listed and briefly explained below:
- Use a strong and separate password for your email – as this is often your route to accessing other accounts.
- Create strong passwords using three random words – this will give you stronger and more memorable passwords.
- Save your passwords in your browser – this prevents you forgetting or losing them.
- Turn on two-factor authentication – this adds an extra element of protection even if your password is compromised.
It’s useful to supplement this with additional reminders not to use the same password across multiple accounts for fear that a breach of one leads to breach of all, not to share them with other people because then it’s no longer your password, and not to keep a discoverable record of them. Storing them in a protected location, such as a password manager tool, is fine.
It’s worrying to think that passwords have been around for decades and we’re still getting it wrong. And they’re just one aspect of cybersecurity that we need to be using properly. This doesn’t bode well for cybersecurity more widely.
- is Professor of Cyber Security, University of Nottingham
- This article first appeared on The Conversation




