Though you can’t see them, radio waves are all around you all the time, carrying information. For most people, some of those radio waves are Wi-Fi signals. Wi-Fi is the catchy name an industry alliance came up with to market devices that transmit large amounts of data over short distances using radio waves. The letters don’t stand for anything. Wi-Fi, like broadcast radio and cellular telephone signals, is based on scientific discoveries dating back to the late 19th century. When electrons moving through a wire are made to alternate directions periodically, something magical happens. Electrons in another wire, located at a distance,…
Author: The Conversation
TV viewing has become more important during the pandemic, but a sense of shame still lingers around it. Even TV scholars still use the term “guilty pleasures” to describe their enjoyment of reality TV or series which attract some of the biggest viewing audiences, such as I’m A Celebrity Get Me Out of Here, The Voice or Dancing With the Stars. Some even call comforting, escapist dramas like Death in Paradise or Bridgerton their “guilty pleasures”. Such television still attracts the same negative labels (“unchallenging”, “low brow”) that were given to its antecedents in the 1950s. I remember the pleasure…
It’s hard to imagine navigating modern life without a mobile phone in hand. Computers, tablets and smartphones have transformed how we communicate, work, learn, share news and entertain ourselves. They became even more essential when the COVID-19 pandemic moved classes, meetings and social connections online. But few people realize that our reliance on electronics comes with steep environmental costs, from mining minerals to disposing of used devices. Consumers can’t resist faster products with more storage and better cameras, but constant upgrades have created a growing global waste challenge. In 2019 alone, people discarded 53 million metric tons of electronic waste. In our work as sustainability…
Facebook made news this week by blocking U.S. President Donald Trump from posting to its platform. A seperate power struggle between government and Big Tech that will be far more consequential in the long term is unfolding in the background. The United States government seems prepared to rein in the social media giant and potentially break up the company. In December 2020, the Federal Trade Commission (FTC) and attorneys general from 46 states launched antitrust proceedings. After months of theatrical congressional testimony by various tech CEOs, this development represents an escalation that could ultimately determine the balance of power between the U.S. government and Silicon Valley. Antitrust is…
Sales of exercise gear and technology-based fitness tools have exploded in the U.S. as people try to maintain their workout regimens without going to the gym. Purchases range from simple dumbbells and outdoor bicycles to internet-connected devices such as the Peloton stationary bike or the Tonal digital weight machine. There are exercise video games like Nintendo’s Wii Fit and PS-2’s Eye Toy: Kinetic; wearable technology like Fitbits or Apple Watches; and mobile apps like Strava. People are even using platforms like Zoom or Skype to connect with a personal trainer. These connected fitness tools bring together your exercise workouts and your digital life. As researchers…
The restrictions associated with the COVID-19 pandemic drove life online in 2020, where it will probably remain for much of 2021. The way we communicate quickly pivoted to Zoom meetings, remote learning and messaging on social media. And in the absence of face-to-face interactions, people quickly became more reliant on emojis to help express their thoughts and feelings to an audience they can no longer see in person. The digital shift has made the emoji an integral part of written language. Ninety-two per cent of consumers online use some form of emoji in their communications. On Instagram, nearly half of the posts contain emojis. In 2015, the Oxford Dictionary went so…
Bitcoin continues to trade close to its all-time high reached this month. Its price recently reached around US $34,000 — up about 77% over the past month and 305% over the past year. First launched in 2009 as a digital currency, Bitcoin was for a while used as digital money on the fringes of the economy. It has since become mainstream. Today, it’s used almost exclusively as a kind of “digital gold”. That is to say, a scarce digital asset. In response to the risk of economic collapse due to COVID, governments around the world have flooded global markets with money created…
What is the cost of propaganda, misinformation and conspiracy theories? Democracy and public safety, to name just two things. The United States has received a stark lesson on how online propaganda and misinformation have an offline impact. For months, Donald Trump has falsely claimed the November presidential election was rigged and that’s why he wasn’t re-elected. The president’s words have mirrored and fed conspiracy theories spread by followers of the QAnon movement. While conspiracy theorists are often dismissed as “crazy people on social media,” QAnon adherents were among the individuals at the front line of the storming of Capitol Hill.…
Spotify offered the promise that, in the age of digital downloads, all artists would get paid for their music, and some would get paid a lot. Lorde and Billie Eilish showed what was possible. Lorde was just 16 when, in 2012, she uploaded her debut EP to SoundCloud. A few months later, Sean Parker (of Napster and Facebook fame) put her first single — “Royals” — on his popular Spotify Hipster International playlist. The song has sold more than 10 million copies. Eilish’s rags-to-riches story is a little murkier. But the approved narrative begins in 2015, when the 13-year-old uploaded “Ocean Eyes” (a…
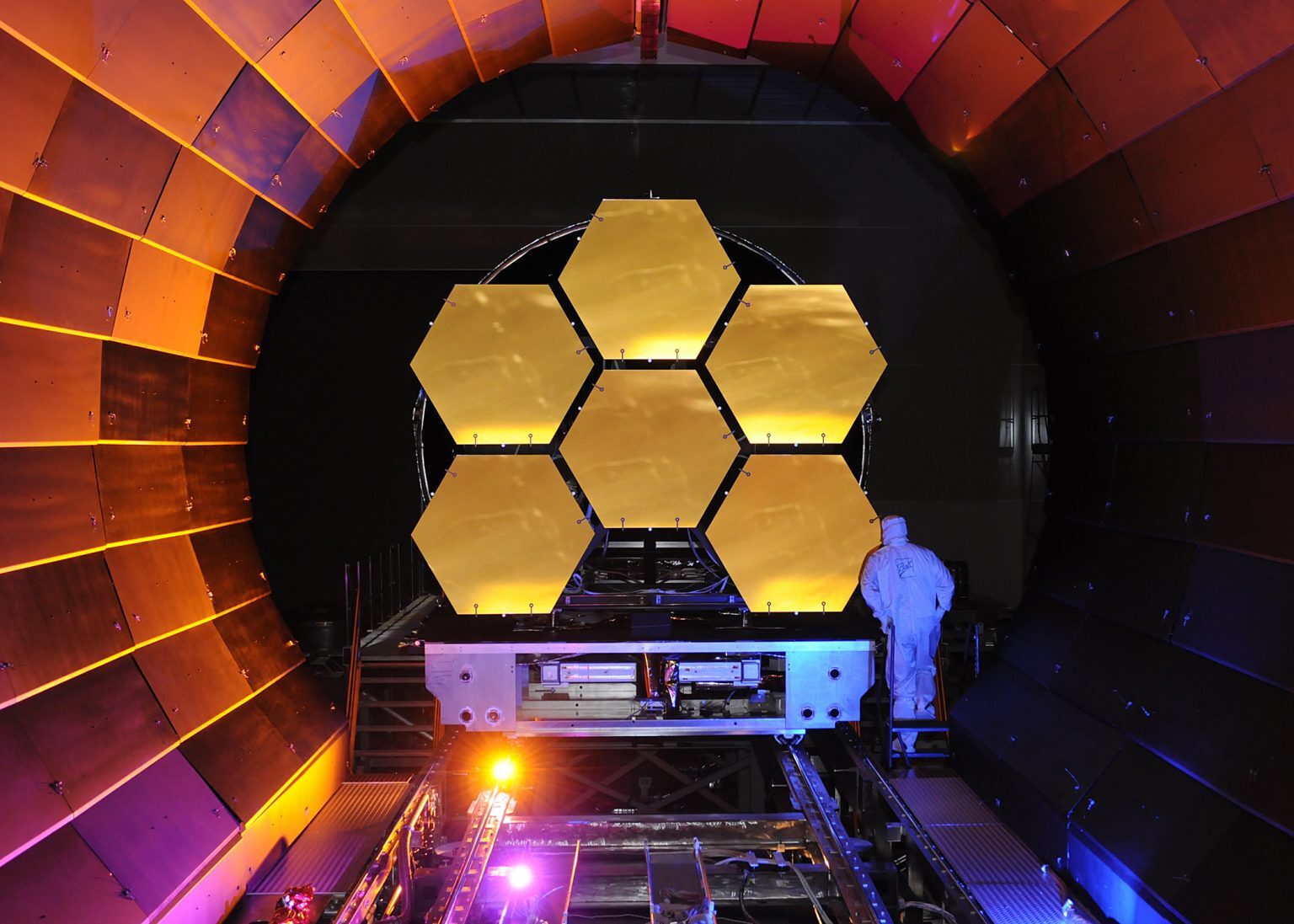
Space exploration achieved several notable firsts in 2020 despite the COVID-19 pandemic, including commercial human spaceflight and returning samples of an asteroid to Earth. The coming year is shaping up to be just as interesting. Here are some of the upcoming space missions to keep an eye out for. Artemis 1 Artemis 1 is the first flight of the Nasa-led, international Artemis program to return astronauts to the Moon by 2024. This will consist of an uncrewed Orion spacecraft which will be sent on a three-week flight around the Moon. IT will reach a maximum distance from Earth of 450,000km – the farthest into space that…