Unless you’re blind or know someone who is, you might not know that blind people use the same smartphones as sighted people. In fact, many blind people use touch-screen smartphones every day. The secret is that smartphones have a screen reader, a tool that allows blind people to use a mix of gestures and taps, along with vibrations or audio feedback, to use their apps. Screen readers work on desktop computers as well as mobile devices. You can usually find the screen reader in settings under accessibility. On iPhones the screen reader is VoiceOver. It provides a verbal description of what’s…
Author: The Conversation
Most of us benefit every day from the fact computers can now “understand” us when we speak or write, thanks to machine learning. Yet few of us have paused to consider the potentially damaging ways this same technology may be shaping our culture. Human language is full of ambiguity and double meanings. For instance, consider the potential meaning of this phrase: “I went to project class”. Without context, it’s an ambiguous statement. Computer scientists and linguists have spent decades trying to program computers to understand the nuances of human language. And in certain ways, computers are fast approaching humans’ ability…
The manufacturing world is facing one of its greatest challenges in years — a global shortage of semiconductors — and there doesn’t appear to be an end in sight any time soon. According to Acer, one of the world’s largest laptop manufacturers, companies will still be affected by this shortage until at least the first half of 2022. Semiconductors are an essential component of electronic devices, found in everything from cars and factory machinery to dishwashers and mobile phones. They harness the conducting properties of semiconductor materials (such as silicon), through the use of electric or magnetic fields, light, heat or…
Digital video surveillance systems can’t just identify who someone is. They can also work out how someone is feeling and what kind of personality they have. They can even tell how they might behave in the future. And the key to unlocking this information about a person is the movement of their head. That is the claim made by the company behind the VibraImage artificial intelligence (AI) system. (The term “AI” is used here in a broad sense to refer to digital systems that use algorithms and tools such as automated biometrics and computer vision). You may never have heard of it,…
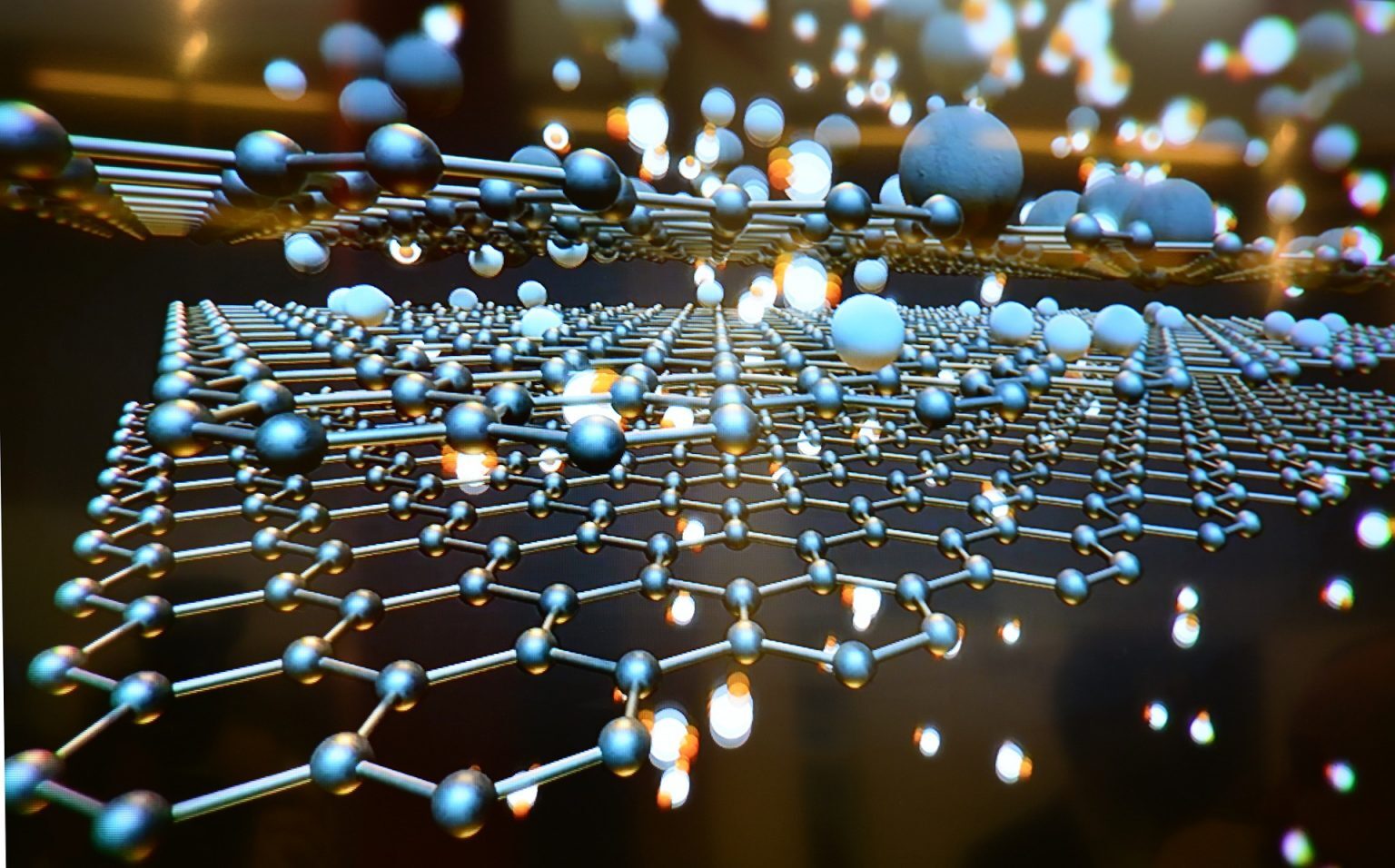
Graphene is a material made of carbon atoms one layer thick, arranged in a honeycomb structure. It has been used to make materials stronger, create ultra-high frequency components for communications, boost battery performance and even used to make COVID-19 tests. It’s the archetypal two-dimensional (2D) material – but there’s much more to 2D materials than graphene. Since graphene was first isolated in 2004, research has expanded to the creation of other, non-carbon 2D materials. Now there are many tens of these, and they’re hailed to make an impact where graphene is less suited, such as in novel transistors and next-generation optoelectronic…
You have probably seen satellite images of the planet through applications like Google Earth. These provide a fascinating view of the surface of the planet from a unique vantage point and can be both beautiful to look at and useful aids for planning. But satellite observations can provide far more insights than that. In fact, they are essential for understanding how our planet is changing and responding to global heating and can do so much more than just “taking pictures”. It really is rocket science and the kind of information we can now obtain from what are called Earth observation…
A defining characteristic of the way many people live today is persistent online connectedness. Since the introduction of smartphones about 15 years ago, the rapid and broad adoption of these devices has had an impact on people’s behaviour at all hours of the day. Forecasts suggest that the number of smartphone connections in sub-Saharan Africa will reach 678 million by the end of 2025, representing an adoption rate of 65%. Many people check their phones when they wake up, use them while travelling to work and constantly keep an eye on them while at work. A phone screen is the last thing many see before…
Tech giant Microsoft recently announced the retirement of its longstanding web browser, Internet Explorer, in favour of its newer product, Microsoft Edge. With support for Internet Explorer only set to last until June 15, 2022, its remaining users have just over a year to find an alternative. But of course, most web users already have. While the eventual downfall of Internet Explorer was seen as a foregone conclusion by those who monitor web trends, the news might come as an unwelcome surprise for those who are somewhat less up-to-date. For the most part, though, this news is a whimper rather…
Within seconds after reaching a city, earthquakes can cause immense destruction: Houses crumble, high-rises turn to rubble, people and animals are buried in the debris. In the immediate aftermath of such carnage, emergency personnel desperately search for any sign of life in what used to be a home or office. Often, however, they find that they were digging in the wrong pile of rubble, and precious time has passed. Imagine if rescuers could see through the debris to spot survivors under the rubble, measure their vital signs and even generate images of the victims. This is rapidly becoming possible using…
If you’re an iPhone user, check your storage now by selecting Settings, then General and then iPhone Storage. You’ll probably see a lot of recognisable categories eating up your storage — apps, photos, and so on. But there is one, often rather large category, that may raise concerns: “Other”. It’s shaded light grey and often represents a significant proportion of the overall storage available. There is one, often rather large category, that often raises concerns: ‘other’. Author provided What is ‘Other’? For more detail, scroll down and tap the “Other” category (right at the end). It doesn’t say much — just…