Recently, when I opened Instagram, I noticed that the usual spot for checking notifications is now a Shop tab. The Instagram blog post announcing the redesign said that the change will support small businesses and connect people with their favorite brands and creators. This made me pause. As a researcher who studies social media, people and society, I’m concerned about the effects of surveillance capitalism. This includes social media companies profiting from collecting user data, making algorithmic inferences about people’s preferences and using this information to target people with advertising. Features like Instagram’s Shop tab facilitate surveillance capitalism, so it’s important to look at…
Author: The Conversation
In Lewis Carroll’s Victorian classic Through the Looking-Glass, Alice steps through a mirror into a world that is a reflection of the one she already exists in. This fictional account of a familiar yet topsy-turvy reality resonates with our lived experiences during the pandemic, where we must navigate work, school and leisure through a screen. Using our combined observations of hundreds of Zoom meetings and scholarly insights from the fields of anthropology and psychology, we explore these questions to consider the transformative impact of digital platforms on our work environments and identities. As the legendary Aretha Franklin asks, “who’s zoomin’ who,”…
Have you been hitting the gym again with COVID restrictions easing? Or getting back into running, cycling, or playing team sports? As many of you might’ve experienced, the inevitable muscle soreness that comes after a break can be a tough barrier to overcome. Here’s what causes this muscle soreness, and how best to manage it. What is muscle soreness and why does it occur? Some muscle soreness after a workout is normal. But it can be debilitating and deter you from further exercise. The scientific term used to describe these aches is delayed onset muscle soreness, or DOMS, which results from…
The COVID-19 pandemic has made it clearer than ever that we are at risk of losing control of our economies. Our institutions have increasingly struggled to meet the challenges of economic development before the crisis, and yet throughout the pandemic we’ve seen surging stock market valuations of tech giants — including staggering CEO salaries — the inability of anti-trust regulators, particularly in the United States, to effectively regulate markets and the rise of China’s tech companies. Tech giants are not just surviving the pandemic; they’re thriving. The superstar economy What’s known as the superstar economy is one with a few hyper-productive, gigantic and highly profitable companies. Superstar firms such as…
Astronomers have mapped about a million previously undiscovered galaxies beyond the Milky Way, in the most detailed survey of the southern sky ever carried out using radio waves. The Rapid ASKAP Continuum Survey (or RACS) has placed the CSIRO’s Australian SKA Pathfinder radio telescope (ASKAP) firmly on the international astronomy map. While past surveys have taken years to complete, ASKAP’s RACS survey was conducted in less than two weeks — smashing previous records for speed. Data gathered have produced images five times more sensitive and twice as detailed as previous ones. What is radio astronomy? Modern astronomy is a multi-wavelength enterprise. What do we…
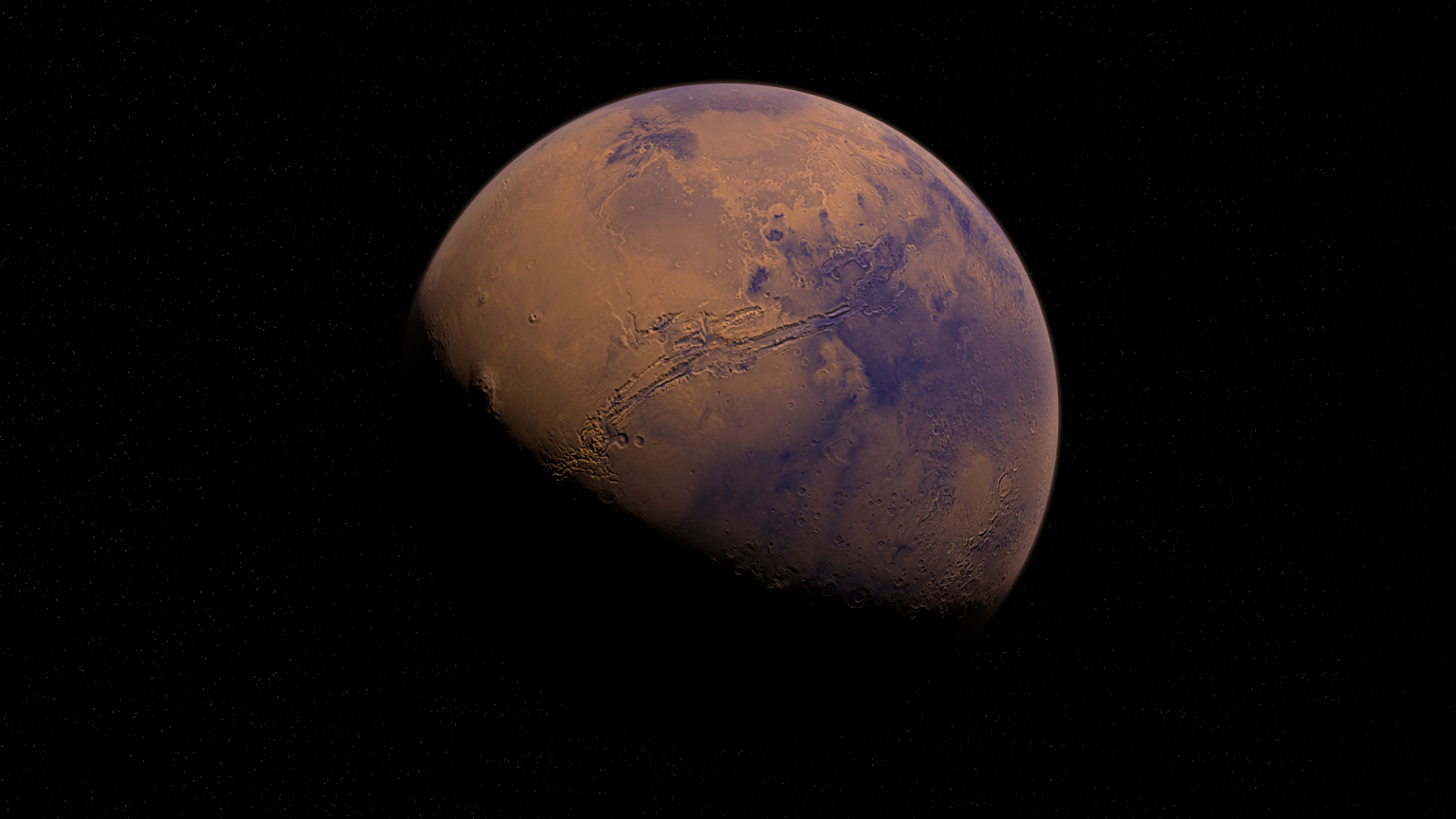
NASA is planning to land a crew on the Moon by 2024, and then onward to Mars, possibly in the 2030s. One day, we will have permanently crewed bases on both worlds. Unlike the initial short-stay visits, long-term bases will have to be self sufficient in as many essentials as possible. A lot of research has gone into preparing for In Situ Resource Utilization (ISRU) that could help to build and sustain a lunar base. Now, similar ideas for Mars are catching up, with a new study, published in PNAS, suggesting a way to use the brine (salty water) found on Mars to make breathable air…
Facebook CEO Mark Zuckerberg’s own words play a starring role in the government’s case to break up his social network. “It is better to buy than compete,” he allegedly wrote in an email in 2008, according to the lawsuit. Four years later, after Facebook purchased what he had called a “very disruptive” photo-sharing app, he celebrated by explaining to a colleague in another email: “Instagram was our threat. … One thing about startups though is you can often acquire them.” As an antitrust professor preparing a new spring course called “Antitrust for Big Tech,” I read the FTC’s Dec. 9 complaint with great…
In a world of countless entertainment opportunities, movies are one of the few remaining proven ways to attract a new audience and retain existing ones. Yet the dominant narrative seems to be that in the age of the internet the old system of theatrical release can no longer cater for audiences worldwide – or so we are told. Digital technologies – streaming in particular – are expected to replace the legacy of theatrical releases, bringing movies into the fold of the growing Direct-to-Consumer (DTC) list of industries, as opposed to third-party distribution through theatrical release. This particular story of the new supplanting the…
Imagining future cities has long been a favourite activity for architects, artists and designers. Technology is often central in these schemes – it appears as a dynamic and seemingly unstoppable force, providing a neat solution to society’s problems. But our recent research has suggested that we need to significantly rethink the way we imagine future cities, and move our focus from an overarching technological vision to other priorities, such as environmental sustainability and the need to tackle social inequalities. We need to answer questions about what can be sustained and what cannot, where cities can be located and where they cannot, and…
Since time immemorial, humans have been fascinated by the night sky. Our relationship with it was forever changed in the early 1600s, when Galileo Galilei raised a small hand-held telescope to the sky and became the first person to see Jupiter’s moons and Saturn’s rings. Optical telescopes today range from pocket telescopes just a few inches long, to the colossal Thirty Meter Telescope being built in Hawaii (which will weigh more than 1,400 tonnes). There are even bigger arrays of telescopes that observe in radio wavelengths, such as the Square Kilometre Array Pathfinder (SKAP) radio telescope. These large telescopes used for research don’t have…