Reducing carbon emissions from roads, railways and shipping requires implementing a range of solutions simultaneously. As far as cars are concerned, cutting the number of journeys altogether (by making it easier for people to walk and cycle and improving public transport), changing the fuel in vehicles and making the most of those vehicles already on the road must all play a part. None of these solutions are sufficient on their own. In 2030, the sale of new diesel and petrol passenger cars will be outlawed in the UK. The future of passenger motoring will be electric. But recent problems supplying parts and the high carbon…
Author: The Conversation
Deepfakes are video, audio and image content generated by artificial intelligence. This technology can produce false images, videos or sounds of a person, place or event that appear authentic. In 2018, there were approximately 14,698 deepfake videos circulating online. Since then, the number has soared through the popularity of deepfake apps like DeepFaceLab, Zao, FaceApp and Wombo. Deepfakes are used in several industries, including filmmaking, video games, fashion and e-commerce. However, the malicious and unethical use of deepfakes can harm people. According to research by cybersecurity firm Trend Micro, the “rise of deepfakes raises concern: It inevitably moves from creating fake celebrity pornographic videos to manipulating company…
The European Space Agency’s (Esa) Gaia mission has just released new data. The Gaia satellite was launched in 2013, with the aim of measuring the precise positions of a billion stars. In addition to measuring the stars’ positions, speeds and brightness, the satellite has collected data on a huge range of other objects. There’s a lot to make astronomers excited. Here are five of our favourite insights that the data might provide. 1. Secrets of our galaxy’s past and future Everything in space is moving, and the stars are no exception. The latest release of data contains the largest three-dimensional map of the…
The streaming wars are heating up. In March, Disney delayed the release date of Obi-Wan Kenobi to May 27 to coincide with the launch of Netflix’s top show, Stranger Things. This on the back of Google’s announcement YouTube Shorts had matched TikTok’s 1.5 billion subscribers in the short-form video market. Facing increased competition, falling subscriber numbers and loss of content, Netflix and TikTok are having to diversify. And for this they’re turning to games. With more than three billion players worldwide, and an estimated market share of US$200 billion, the gaming industry is both popular and lucrative. Netflix introduced mobile gaming last year for all its subscribers. This included two notable Stranger…
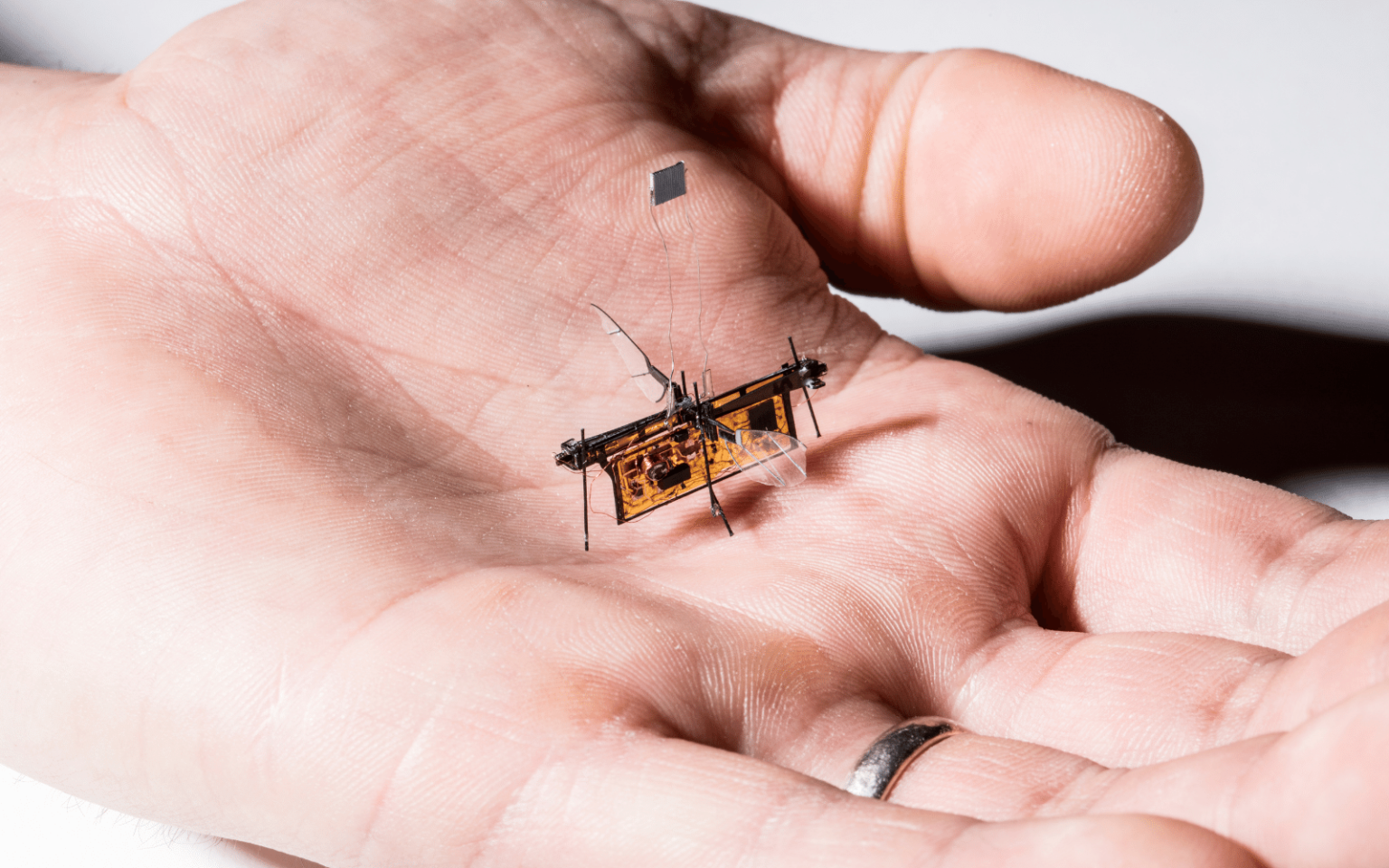
Allow me to take you on a trip down my memory lane. As a young lad, a film I saw captured my imagination: Fantastic Voyage, a 1966 release about people shrunk to microscopic size and sent into the body of an injured scientist to repair his brain. The idea struck a chord with me. I envisioned one day science would be able to create some sort of miniature machine that performs medical procedures from the inside. Fast forward several decades into the 21st century, when I started my career as a robotics researcher taking inspiration from neuroscience to implement artificial perception…
When one of our students told us they were going to drop out of college in August 2021, it wasn’t the first time we’d heard of someone ending their studies prematurely. What was new, though, was the reason. The student had become a victim of a cryptocurrency scam and had lost all their money – including a bank loan – leaving them not just broke, but in debt. The experience was financially and psychologically traumatic, to say the least. This student, unfortunately, is not alone. Currently there are hundreds of millions of cryptocurrency owners, with estimates predicting further rapid growth. As…
Increases in the domestic price of fuel are big news in South Africa, with the price of petrol, diesel and paraffin reaching new highs. The underlying reason for the price increases is movements in the international price of crude oil. The acceleration in the international price of crude oil is linked to the Russian war in the Ukraine. The expectation is that the crude oil price will remain at an elevated level for the duration of the war. Internationally, crude oil is priced in US dollar per barrel. Recently the price exceeded US$120 per barrel. This is not the highest level ever for the crude oil…
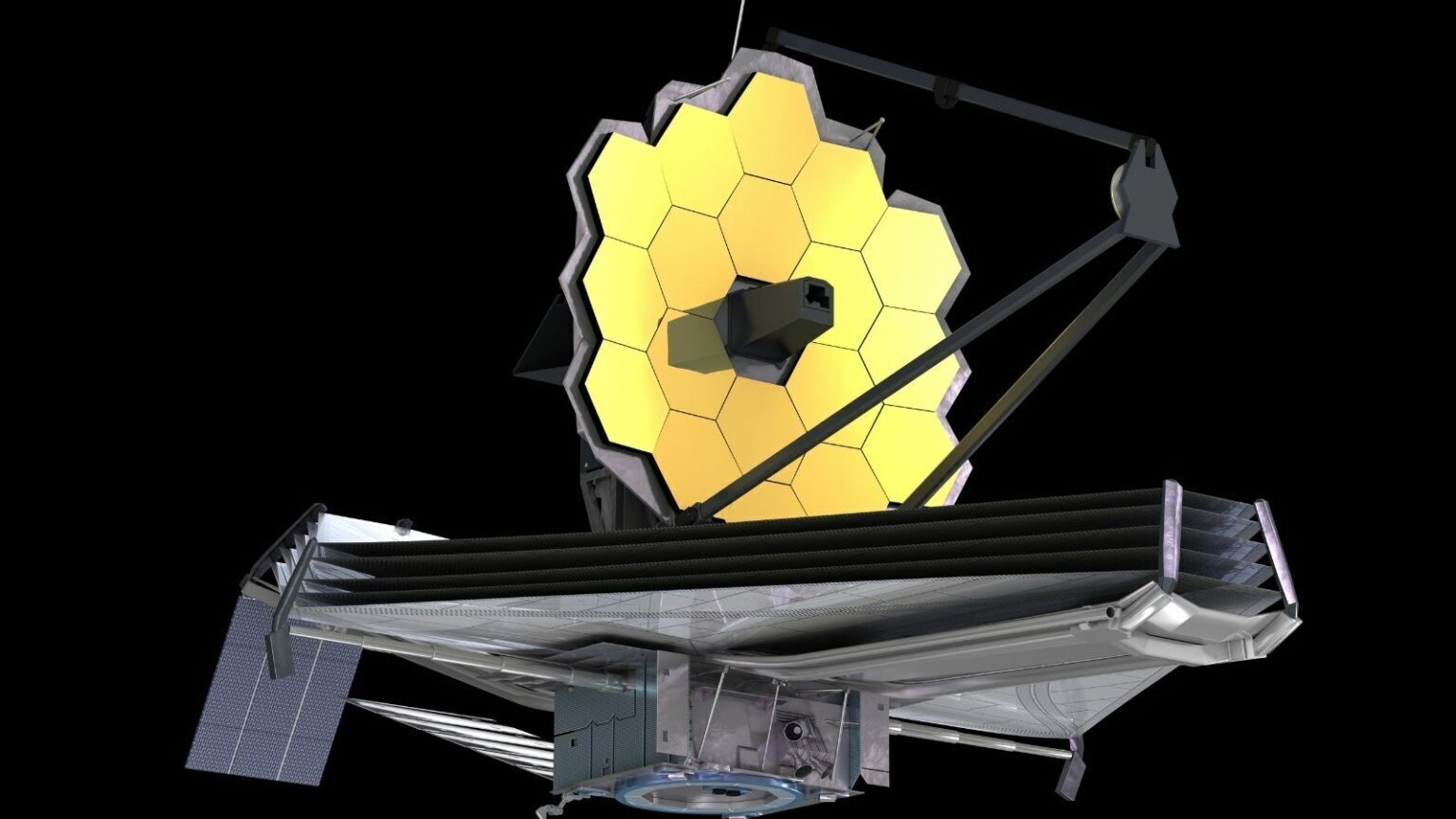
NASA is scheduled to release the first images taken by the James Webb Space Telescope on July 12, 2022. They’ll mark the beginning of the next era in astronomy as Webb – the largest space telescope ever built – begins collecting scientific data that will help answer questions about the earliest moments of the universe and allow astronomers to study exoplanets in greater detail than ever before. But it has taken nearly eight months of travel, setup, testing and calibration to make sure this most valuable of telescopes is ready for prime time. Marcia Rieke, an astronomer at the University of…
Technology has increasingly blurred the boundaries between the physical and digital worlds. This has led to dramatic shifts in daily life and changed the way children and adolescents live, socialise, move around and learn. Never before has this been so evident than at the onset of the COVID pandemic and the subsequent exponential rise in technology and internet use. Global estimates suggest that one in three internet users is a child. Digital technology exposes children to information, social connection, education, online support groups and professional help. Yet, children engaging in the digital world are also exposed to a range of threats. These include inappropriate…
It’s hard to imagine that three random words have the power to both map the globe and keep your private data secure. The secret behind this power is just a little bit of math. What3words is an app and web-based service that provides a geographic reference for every 3-meter-by-3-meter square on Earth using three random words. If your brain operates more naturally in the English measurement system, 3 meters is about 9.8 feet. So, you could think of them as roughly 10-foot-by-10-foot squares, which is about the size of a small home office or bedroom. For example, there’s a square in…