In the latest salvo of an almost two-decade console war between Microsoft and Sony, both Sony’s Playstation 5 and Microsoft’s…
Browsing: The Conversation
The Assassin’s Creed franchise is leaping forward (off the top of a building, presumably) with the release of the 12th…
Many professionals, including academics, are accustomed to flying a lot. Or they were before COVID-19 drastically reduced air travel and disrupted conference…
We were used to consuming architecture – both near to home and far away – with ease. But this year,…
As you drive down the road leading to Jodrell Bank Observatory, a sign asks visitors to turn off their mobile…
About a year ago I began to follow my interest in health and fitness on Instagram. Soon I began to…
The most effective way to stop the spread of a virus is to prevent contact with everyone who is infected.…
Every day, Americans travel on roads, bridges and highways without considering the safety or reliability of these structures. Yet much…
As new social restrictions are imposed to combat the spread of COVID-19, it will be no surprise if people once…
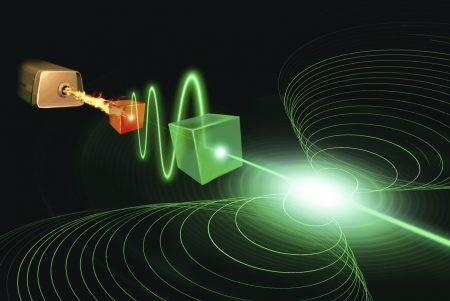
Lasers were created 60 years ago this year, when three different laser devices were unveiled by independent laboratories in the…