Blockchain denialists will tell you that the decentralised technology ‘doesn’t do anything new’ and that it ‘results in the same outcome, just with extra steps’. Yet, new research has surfaced detailing a rather clever way malicious internet denizens are using one example of the technology to keep their malware safe from the Feds. See, denialists, blockchain can be useful.
We’ll admit that ‘useful’ in this case is heavily dependent on which side of the malware you find yourself. If it’s not your malware then ‘useful’ probably isn’t the first word that comes to mind.
Using new tech for old tricks
One of the oldest tricks used by nefarious individuals to steal personal information is duping someone into signing in to a lookalike site or service or downloading an info-stealing trojan.
In this case, ClearFake, as security researcher Randy McEoin calls it, is a type of malware that uses compromised WordPress websites to trick unsuspecting people into downloading a supposed browser update before they can continue. It even goes so far as to detect which browser the victim is using to provide the ‘right’ malicious update alert.
If you fall for the trick and click ‘update’, you’ll download a file which will install the aforementioned info-stealing trojan. To combat this kind of scam, authorities target the source of the malicious files to stop them from spreading.
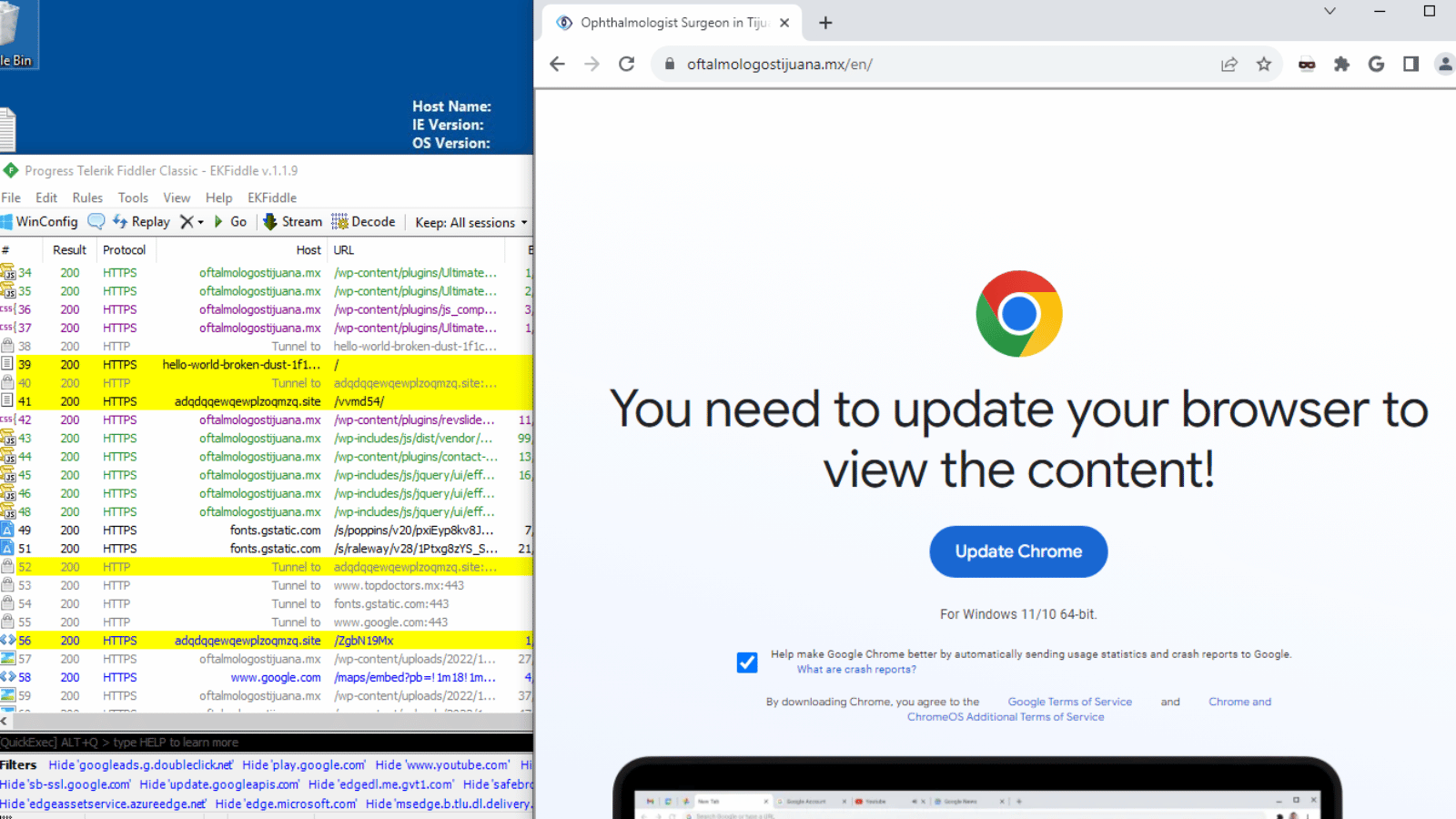
However, according to researchers at Guardio, a Tel Aviv-based security firm, when Cloudflare blocked the malicious ClearFake accounts, the group opted to store their malware in the Binance Smart Chain (BSC) disguised as cryptocurrency transactions.
This improved ClearFake scam still uses compromised WordPress sites, only now it creates a new smart contract using “a unique, attacker-controlled blockchain address and a set of instructions that defines the contract’s functions and structure,” writes Nati Tal, head of security at Guardio’s research unit, Guardio Labs.
“Due to the publicly accessible and unchangeable nature of the blockchain, code can be hosted “on-chain” without the ability for a takedown.”
What now, blockchain stans?
According to KrebsOnSecurity, the team behind the Binance Smart Chain said it was aware of and actively addressing the issue by blacklisting the blockchain addresses associated with the malware group. It also said its technicians have developed a way to detect when future smart contracts use similar methods of hiding malware.
As plausible as the BSC team’s response sounds, this definitely isn’t the kind of attention that blockchain enthusiasts enjoy.
Next time you’re browsing the web and are offered an update you didn’t ask for, maybe think twice before accepting.
